-
利用ns实现ddns
ddns的工具有很多,比如softether-vpnserver,花生壳,或者用阿里云,腾讯云dns服务器的接口实现等
但如果这几种都不能使用的话,可以尝试用ns记录解析到自己的dns服务器,自己搭建的dns服务器利用shell动态更新地址1.centos7搭建dns服务器,前提需要有个固定外网地址
yum install bind-chroot
开机启动:
systemctl enable named-chroot配置bind
vim /etc/named.conf 改完后的配置如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62options {
listen-on port 53 { any; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { any; };
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable yes;
dnssec-validation yes;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.iscdlv.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
zone "zydyh.net" IN {
type master;
file "zydyh.net.zone";
};
#zone "f.com" IN {
# type master;
# file "f.com.zone";
#};
#
##zone "0.168.192.in-addr.arpa" IN {
# type master;
# file "192.168.0.zone";
#};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";默认配置修改这两项:
listen-on port 53 { any; }表示监听任何ip对53端口的请求
allow-query { any; }表示接收任何来源查询dns记录
zone “zydyh.net” IN {
type master;
file “zydyh.net.zone”;
};
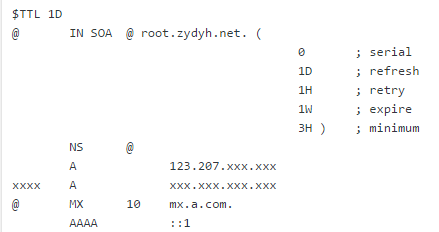
这里增加一个zydyh.net域名的解析,具体解析规则在/var/named/zydyh.net.zone里。
反向解析根据需要看是否配置,我这边没有配置配置/var/named/zydyh.net.zone文件, 注意这个文件named用户需要权限
2.dnspod上设置ns
域名服务器解析如下:
A记录: 将域名指向一个IPv4地址(例如:8.8.8.8)
CNAME:将域名指向另一个域名(例如www.qcloud.com)
MX: 将域名指向邮件服务器地址
TXT: 可任意填写,长度限制255,通常做SPF记录(反垃圾邮件)
NS: 域名服务器记录,将子域名指定其他DNS服务器解析
AAAA:将域名指向一个iPv6地址(例如:ff06:0:0:0:0:0:0:c3)
SRV:记录提供特定服务的服务器(例如_xmpp-server._tcp)
显性URL:将域名301重定向到另一个地址
隐性URL:类似显性URL,但是会隐藏真实目标地址这里有一个坑,ns不能直接写ip地址,至少我写ip时不能解析,只能换成域名,先设个A记录,然后ns到这个域名上
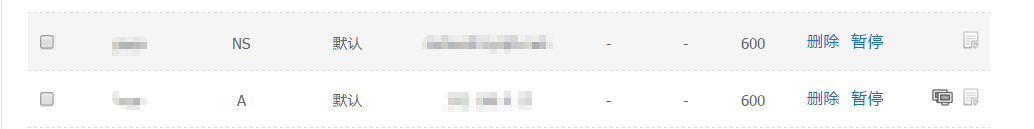
3.利用shell自动更新地址
这个只要在客户机上获取到真实外网地址,然后更新/var/named/zydyh.net.zone文件,脚本自己写啦,我这里用了md5sum命令来判断文件是否被修改
systemctl restart named-chroot





大神,这么强